
As great as WordPress is, there are a few things about it that seriously annoy me. While the razzmatazz of this CMS is impressive, you might be failing to notice some basic security settings that could make the difference between being hacked and being left alone.
Make no mistake – hackers will target ANY WordPress blog because the attempts are often made by automatic sub routines scouring the web daily for vulnerablities.
Millions of malicious bots scan WordPress sites for weak usernames and passwords to reveal vulnerabilities.
These are called brute force attacks and that’s what I want to draw your attention to right now.
A tutorial video is included at the end.
WordPress Username Vulnerabilities
I’m guessing you have already changed your WordPress username from the default “admin” to something hard to guess?
Good, that’s a start.
But if I had a penny for every time a WordPress website owner didn’t change their user_nicename in phpMyAdmin I’d have enough to buy a good steak dinner.
It may be you’ve never even heard of user_nicename. That’s okay. Some of the top bloggers don’t even know about this.
Everything will become clear after I explain what this has to do with website security and how it concerns your URL.
WordPress User Security
Look at the screenshot below. What do you see in the last part of the URL?
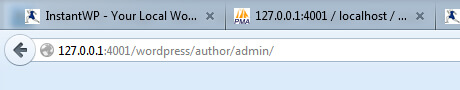
In case the image hasn’t loaded, here’s a reiteration below:
/author/admin/
That, my friend, is your WordPress username.
Even if you change it to something other than “admin” it will still show up in the author archive URL.
It’s a dead give away. Go to any WordPress site, and look for the Posted by section under the title of a post.
Unless the webmaster has already configured the database to show something different, you’ll be able to find out what that webmaster’s logging in name is!
It’s crazy!
This is a general WordPress problem that CAN be corrected in phpMyAdmin.
If you don’t take steps to resolve this now, you are leaving yourself wide open to potential attack.
Think about it: you’re giving potential hackers part of what they need to begin a brute force automatic hacking campaign to try and access your site!
Once they have your username, they just need your password (and most people use a weak password.)
You might get away with it, but is it worth waiting to find out?
The Fix: A Simple phpMyAdmin Tweak
If you follow the instructions I’m about to give you, it is possible to disguise your username by altering how the author URL/slug appears, thus hiding the real username you use to log in.
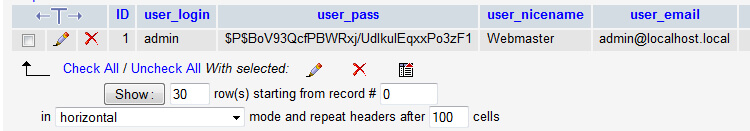
The screenshot below is from phpMyAdmin.
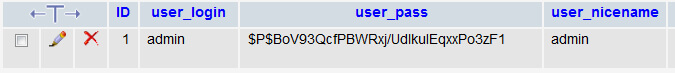
Notice how the user_nicename is identical to the user_login.
It uses “admin” in both instances.
This is our problem. You MUST change the user_nicename to something different.
It doesn’t alter your logging in credentials. It just hides your username from prying eyes.
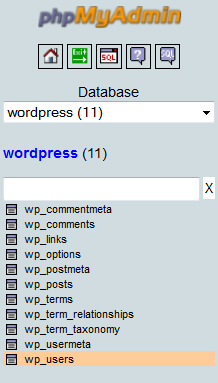
You need to access the table wp_users in your main database inside phpMyAdmin.
If you use cPanel for hosting, you’ll find the phpMyAdmin icon under the databases section.
In the example, the database is called “wordpress”. Your database might be called something different.
Access the correct database and click wp_users.
Then you can change the setting from “admin” (or whatever is showing up in the author archive URL) to something else:
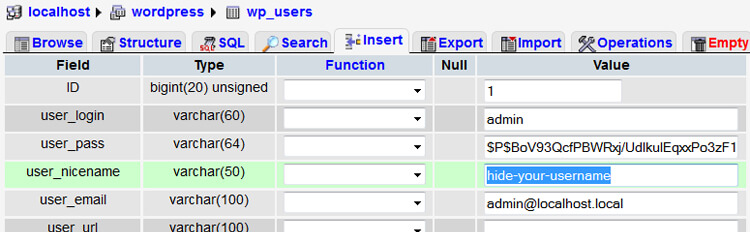
Your version of phpMyAdmin might be a little different depending on your host. Another way to edit the wp_users table is to locate it and click the “browse” icon off to the right.
Click that and you can access and edit the rows containing the user login data.

While you can make this tweak on the live version of your website database, I suggest doing it while you’re in the offline/development phase.
InstantWP is an exact copy of WordPress and you can access the same if not very similar database settings from there.
It’s especially important you do this for client websites you might be developing.
Eventually, you want something that looks a bit like the screenshot below.
(Just don’t use admin as your user_login. The example shown is hypothetical and not even a real website.)
I’ve produced a short video showing you how to solve the issue if my instructions are not clear:
Free WordPress Security Plugin
It is probably worth your while using the WordFence Security plugin for WordPress since this monitors all logins.
They even send you an email digest to let you know which usernames were used as part of a login attempt.
If you run a multiauthor blog this is useful because it shows both authorised and unauthorised logins.